二、部署k8s高可用集群
2.1 高可用集群规划
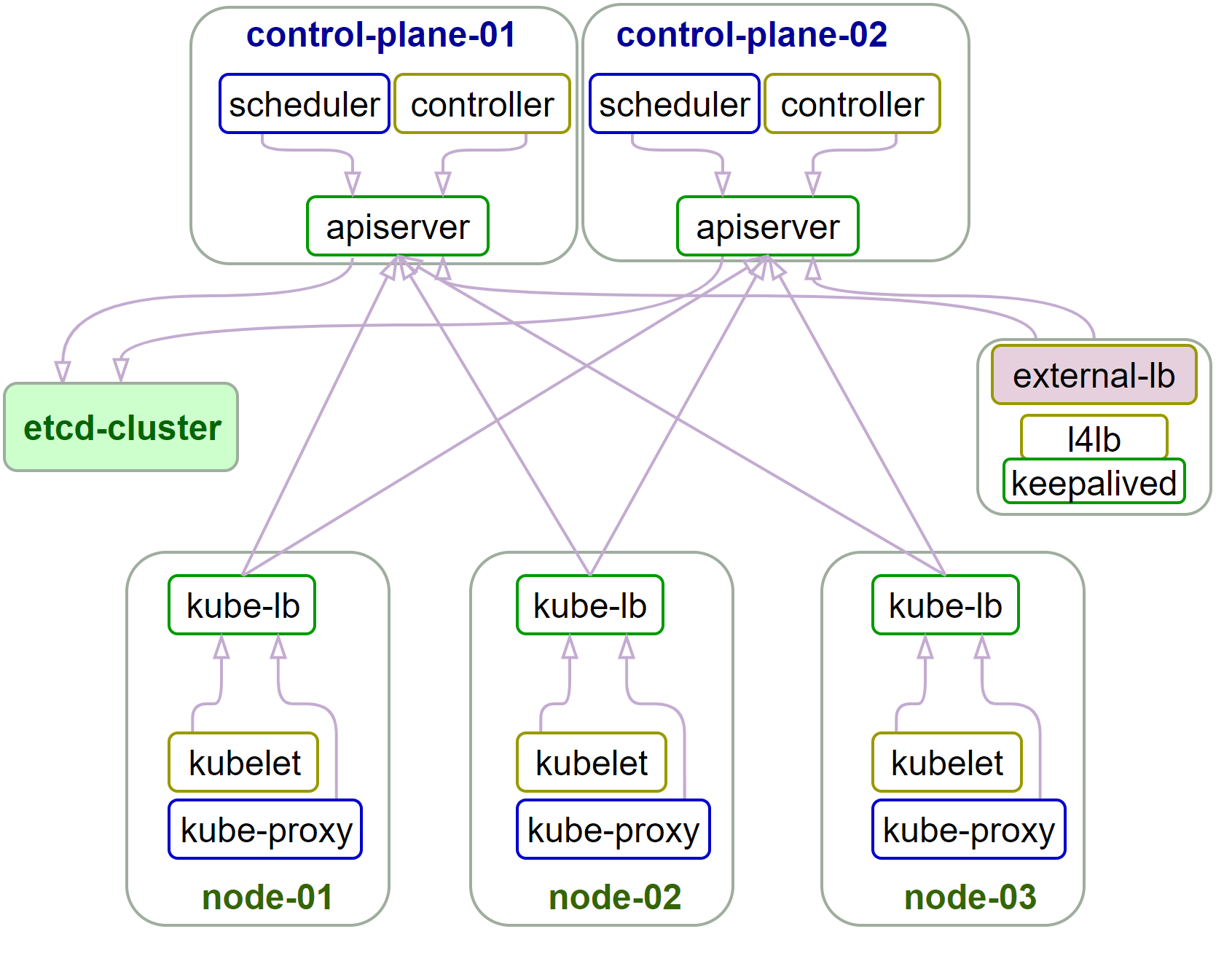
高可用集群构架图大致如下(下图是从官网复制过来的,跟本文中k8s集群节点布局稍有差别,但大致不变):
注意1:确保各节点时区设置一致、时间同步。 如果你的环境没有提供NTP
时间同步,推荐集成安装chrony
注意2:确保在干净的系统上开始安装,不要使用曾经装过kubeadm或其他k8s发行版的环境
注意3:建议操作系统升级到新的稳定内核,请结合阅读内核升级文档
注意4:在公有云上创建多主集群,请结合阅读在公有云上部署
kubeasz
高可用集群所需节点配置如下:
角色
数量
描述
部署节点
1
运行ansible/ezctl命令,一般复用第一个master节点
etcd节点
3
注意etcd集群需要1,3,5,...奇数个节点,一般复用master节点
master节点
3
高可用集群至少3个master节点(上图来自kubeasz官网,只画出两个master节点不准确)
node节点
n
运行应用负载的节点,可根据需要提升机器配置/增加节点数
机器配置:
master节点:4c/8g内存/50g硬盘
worker节点:建议8c/32g内存/200g硬盘以上
注意:默认配置下容器运行时和kubelet会占用/var的磁盘空间,如果磁盘分区特殊,可以设置config.yml中的容器运行时和kubelet数据目录:CONTAINERD_STORAGE_DIR
DOCKER_STORAGE_DIR KUBELET_ROOT_DIR
在 kubeasz 2x 版本,多节点高可用集群安装可以使用2种方式:
1.按照本文步骤先规划准备,预先配置节点信息后,直接安装多节点高可用集群
2.先部署单节点集群 AllinOne部署 ,然后通过
节点添加
扩容成高可用集群
2.2 高可用集群部署步骤
以下示例创建一个5节点的多主高可用集群,最后添加一个节点k8s03-6,文档中命令默认都需要root权限运行。
主机名
IP
root密码
规格
磁盘
操作系统
备注
k8s03-1
10.13.15.61
cloud@2020
8c16g
400G
Ubuntu20.04.3 LTS-amd64
控制节点、Harbor服务器
k8s03-2
10.13.15.62
cloud@2020
8c16g
400G
Ubuntu20.04.3 LTS-amd64
控制节点
k8s03-3
10.13.15.63
cloud@2020
8c16g
400G
Ubuntu20.04.3 LTS-amd64
控制节点
10.13.15.70
多控制节点做keepalived与l4lb后的虚拟ip
k8s03-4
10.13.15.64
cloud@2020
8c16g
400G
Ubuntu20.04.3 LTS-amd64
工作节点
k8s03-5
10.13.15.65
cloud@2020
8c16g
400G
Ubuntu20.04.3 LTS-amd64
工作节点
k8s03-6
10.13.15.66
cloud@2020
8c16g
400G
Ubuntu20.04.3 LTS-amd64
控制节点(演示添加工作节点)
2.2.1 基础系统配置
开发环境每个节点8C核心16G内核/50G磁盘+,生产环境的配置要更高(具体看业务数量。建议直接用128C256G+物理服务器)、磁盘空间建议1T+
最小化安装Ubuntu 16.04+ server或者CentOS 7+ Minimal
配置基础网络、更新源、SSH登录等
推荐使用ansible in docker 容器化方式运行,无需安装额外依赖
2.2.2 在每个节点配置时间同步
2.2.2.1 配置时区
1 2 3 4 5 6 7 # 所有节点时区都配置为东八区 # 手动设置时间为北京时间(尽量靠近准确的北京时间) # 查看时区与时间
2.2.2.2 安装配置时间同步服务
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 # 1.安装 chrony 作为时间同步软件: # 2.修改配置文件 /etc/chrony/chrony.conf,修改 ntp 服务器配置(以下3种方式任选其一): # 2.1 使用默认的 pool 配置 # 2.2 增加国内的 ntp 服务器,或是指定其他常用的时间服务器 # 2.3 若要使用本地NTP服务器,可以将上面的删除,然后添加自己的NTP服务器(假设10.0.0.1是本地NTP服务器):
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 # 重启 chrony 服务: # 验证 chrony 同步状态: # 输出内容大致如下
2.2.3 在每个节点安装依赖工具
推荐使用ansible in docker 容器化方式运行,无需安装额外依赖
2.2.4 安装k8s
k8s与kubeasz推荐的匹配版本对照表:
Kubernetes version
1.19
1.20
1.21
1.22
1.23
1.24
1.25
1.26
1.27
1.28
1.29
1.30
1.31
kubeasz version
2.2.2
3.0.1
3.1.0
3.1.1
3.2.0
3.6.2
3.6.2
3.6.2
3.6.2
3.6.2
3.6.3
3.6.4
3.6.5
2.2.4.1
下载项目源码、二进制及离线镜像
1 2 3 4 5 6 # 下载工具脚本ezdown,举例使用kubeasz版本3.2.0
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 # 下载kubeasz代码、二进制、默认容器镜像(更多关于ezdown的参数,运行./ezdown 查看) # 国内环境(-k指定k8s版本,其他参数执行“./ezdown”查看),以下命令会创建并启动local_registry容器 # 海外环境 # ./ezdown -D -m standard # 下载harbor相关镜像 # 【可选】下载额外容器镜像(cilium,flannel,prometheus等) # ./ezdown -X -m "CN" -k "v1.23.17" # 【可选】下载离线系统包 (适用于无法使用yum/apt仓库情形) # ./ezdown -P -m "CN" -k "v1.23.17"
上述脚本运行成功后,所有文件(kubeasz代码、二进制、离线镜像)均已整理好放入目录/etc/kubeasz
2.2.4.2 创建集群配置实例
1 2 3 4 5 6 7 8 9 10 # 容器化运行kubeasz(会创建并启动kubeasz容器) # 创建新集群 k8s03
然后根据提示配置'/etc/kubeasz/clusters/k8s03/hosts' 和
'/etc/kubeasz/clusters/k8s03/config.yml':根据前面节点规划修改hosts
文件和其他集群层面的主要配置选项;其他集群组件等配置项可以在config.yml
文件中修改。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 # 按住alt键 + 鼠标左键,可以按列选择 # 'etcd' cluster should have odd member(s) (1,3,5,...)# master node(s), set unique 'k8s_nodename' for each node # CAUTION: 'k8s_nodename' must consist of lower case alphanumeric characters, '-' or '.' , # and must start and end with an alphanumeric character # 10.13.15.61 k8s_nodename="k8s03-1" # work node(s), set unique 'k8s_nodename' for each node # CAUTION: 'k8s_nodename' must consist of lower case alphanumeric characters, '-' or '.' , # and must start and end with an alphanumeric character # [optional] harbor server, a private docker registry # 'NEW_INSTALL' : 'true' to install a harbor server; 'false' to integrate with existed one# 192.168.1.8 NEW_INSTALL=false # [optional] loadbalance for accessing k8s from outside # 10.13.15.70是3个控制节点组成keepalived与l4lb集群后的虚拟ip # [optional] ntp server for the cluster # 192.168.1.1 # --------- Main Variables --------------- # Secure port for apiservers # Cluster container-runtime supported: docker, containerd # if k8s version >= 1.24, docker is not supported# CONTAINER_RUNTIME="containerd"
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 root@k8s03-1:/opt/kubeasz-deployk8s# vi /etc/kubeasz/clusters/k8s03/config.yml # k8s version # K8S_VER: "1.23.1" # # role:etcd # # 设置不同的wal目录,可以避免磁盘io竞争,提高性能 # ETCD_DATA_DIR: "/var/lib/etcd" # ETCD_WAL_DIR: "" # # role:runtime [containerd,docker] # # [containerd].................. # SANDBOX_IMAGE: "easzlab/pause:3.6" # [docker].........HTTP...... # INSECURE_REG: '["127.0.0.1/8"]' # nfs-provisioner ............ # # role:harbor # # harbor version..................
2.2.4.3 开始安装
1 2 3 # 以下操作是在k8s节点操作系统上,不是在容器内。也可以进容器kubeasz直接操作 # 建议使用alias 命令,查看~/.bashrc 文件应该包含:alias dk='docker exec -it kubeasz'
2.2.4.3.0 安装配置docker registry
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 root@k8s03-1:/opt/kubeasz-deployk8s# openssl req -addext "subjectAltName = DNS:easzlab.io.local" \
2.2.4.3.1 配置ssh免密登录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 root@k8s03-1:~# cat /etc/hosts# $IP 为所有节点地址包括自身,按照提示输入yes 和root密码# 为每个节点设置python软链接
2.2.4.3.2 搭建nfs服务器
本文以在k8s03-1节点上搭建nfs服务端为例
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 # # 执行以下命令安装 NFS 服务, # apt 会自动安装 nfs-common、rpcbind 等软件包 # 创建作为nfs服务端的根目录 # 编写配置文件 # [任意主机所有权限] # 重启 NFS 服务 # 常用命令工具 # 在安装 NFS 服务器时,已包含常用的命令行工具,无需额外安装 # 显示已经 mount 到本机 NFS 目录的客户端机器 # 将配置文件中的目录全部重新 export 一次,无需重启服务 # 查看 NFS 的运行状态 # 查看 rpc 执行信息,可以用于检测 rpc 运行情况
2.2.4.3.3 一键部署与分步部署
1 2 3 4 5 6 7 8 9 10 11 12 13 # 在k8s节点上操作,当然也可以进容器kubeasz内操作 # 建议使用alias 命令,查看~/.bashrc 文件应该包含:alias dk='docker exec -it kubeasz' # 一键安装,等价于执行docker exec -it kubeasz ezctl setup k8s03 all # 对于不熟悉的操作者而言,建议分步执行,执行完一个步骤后查看此步骤的结果以熟悉整个部署流程 # 或者分步安装,具体使用 dk ezctl help setup 查看分步安装帮助信息 # dk ezctl setup k8s03 01 # dk ezctl setup k8s03 02 # dk ezctl setup k8s03 03 # dk ezctl setup k8s03 04
2.2.4.3.4 01-创建证书和安装准备
1 2 3 4 5 6 # 容器内操作 # 在k8s节点上操作
2.2.4.3.5 02-安装etcd集群
1 k8s03-1:/# ezctl setup k8s03 02
2.2.4.3.6 03-安装容器运行时
1 k8s03-1:/# ezctl setup k8s03 03
2.2.4.3.7 04-安装master节点
1 2 3 4 5 6 7 8 k8s03-1:/# ezctl setup k8s03 04# 上述安装master节点相关命令执行成功后,可以查看集群中的master节点,如下
2.2.4.3.8 05-安装node节点
1 2 3 4 5 6 7 8 9 10 k8s03-1:/# ezctl setup k8s03 05# 上述安装node节点相关命令执行成功后,可以查看集群中的所有节点,如下
2.2.4.3.906-安装集群网络
1 k8s03-1:/# ezctl setup k8s03 06
2.2.4.3.10 07-安装集群插件
1 2 3 4 5 6 7 8 9 10 11 12 k8s03-1:/# ezctl setup k8s03 07# 查看创建的sc # 将sc/managed-nfs-storage 设置为默认的sc
2.2.4.3.11 10-ex-lb
1 k8s03-1:/# ezctl setup k8s03 10
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 # 3个控制节点上现在应该都正常运行了以下两个服务 # 因为默认情况下,k8s03-1 是keepalived 集群的主节点,所以此时VIP 10.13.15.70 应该是在k8s03-1上
2.2.4.3.11.1 负载均衡相关设置
1 2 3 4 5 6 7 8 9 10 11 #
1 2 3 4 5 6 7 8 9 10 11 12 # 回到k8s节点上操作 # NodePort类型的 service/kubernetes-dashboard 在k8s节点上映射的端口是 32268 # 以下使用vip + 32268 即 https://10.13.15.70:32268 来访问kuboard(建议使用 firefox 浏览器访问) # 另外,当然也可以使用k8s集群任何一个节点的IP+32268,以访问kubernetes原生dashboard即kuboard(建议使用 firefox 浏览器访问)
image-20241031173526066
2.2.4.4 查看集群信息与状态
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 # 查看k8s节点列表 # 查看集群中pod列表 # 查看component status
1 2 3 4 5 6 7 8 9 # 查看namespace/kube-system下的svc
2.2.4.5 登录kubernetes-dashboard
image-20250110145004619
选择Kubeconfig时,如果提示“Internal error (500): Not enough data to
create auth info structure.”,请参照如下方式处理:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 # 创建如下3个文件,然后分别apply或bash执行 # !/bin/bash # 上述脚本文件执行时输出如下内容 # 将上述输出内容复制,按如下形式粘贴到/root/.kube/config文件中
使用上述/root/.kube/config 文件即可登录kubernetes-dashboard 。
2.2.5 安装harbor
2.2.5.1 使用默认配置安装Harbor
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 # 如果是彻底重新安装harbor,要先删除harbor服务器上 /var/data/database /var/data/registry /var/data/redis /var/data/job_logs /var/data/harbor 这几个目录 # k8s节点上、kubeasz容器外执行如下命令,查看harbor相关容器 # 安装harbor(kubeasz容器内执行) # 如果是前面安装了ex-lb,则k8s03-1节点上的8443端口将被占用了。而安装harbor时也尝试去使用8443端口,此时此步骤就会在最后阶段失败,即“TASK [harbor : 安装 harbor]”任务失败,"msg" : "non-zero return code" 。 # 所以使用kubeasz安装harbor之前要先将 clusters/k8s03/config.yml 文件中的 HARBOR_TLS_PORT 参数值修改为其他值,比如修改为8444 # k8s节点上、kubeasz容器外执行如下命令,查看harbor相关容器 # harbor的安装目录默认在:/var/data,它由“/etc/kubeasz/clusters/k8s03/config.yml”中的 HARBOR_PATH 配置项决定 # harbor系统admin用户的密码,在harbor部署服务器的如下文件中查看:/var/data/harbor/harbor.yml # Dgyj08NOYtvhMc7x # 在k8s集群所有节点上,可以登录此harbor仓库。用户:admin,密码就是在harbor部署服务器的如下文件/var/data/harbor/harbor.yml中harbor_admin_password 配置值
2.2.5.2 修改Harbor服务的端口
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 root@k8s03-1:~# cd /var/data/harbor# 先停掉harbor相关容器 # 将所有 8444 字符串替换成 8445 # 重新启动harbor相关容器 # 修改证书目录 # 登录 # 尝试提交镜像...
2.2.6 继续安装Kubesphere
本文已经使用kubeasz3.2.0
安装好kubernetes1.23.17,现准备部署kubesphere3.4.1。
前提条件
安装之前,Kubernetes 集群已配置默认 存储类型
(StorageClass);
当使用 --cluster-signing-cert-file 和
--cluster-signing-key-file 参数启动时,在
kube-apiserver 中会激活 CSR 签名功能。请参见 RKE
安装问题 ;(暂时无需关注)
有关在 Kubernetes 上安装 KubeSphere 的准备工作,请参见准备工作 。
2.2.6.1 手动创建sc/local
使用kubeadm或kubeasz部署的k8s环境,没有创建任何storage
class资源对象,需要自己创建。一个默认的sc是部署的kubesphere的前提条件。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 root@k8s03-1:~# cd /etc/kubeasz/clusters/k8s03/# 应用上述yaml文件,创建local sc # 设置为默认StorageClass # kubectl patch storageclass local -p '{"metadata": {"annotations":{"storageclass.kubernetes.io/is-default-class":"true"}}}' # 集群中创建默认StorageClass # 默认没有,可以自建 # 创建 StorageClass:https://kubernetes.io/zh-cn/docs/concepts/storage/storage-classes/ # 设置默认 StorageClass:https://kubernetes.io/zh-cn/docs/tasks/administer-cluster/change-default-storage-class/
2.2.6.2 手动创建sc/nfs
1 # 在k8s03-1节点上搭建nfs服务端:参考“2.2.4.3.2 搭建nfs服务器”章节
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 # 1 下载并创建storageclass # 将nfs-client sc设置为默认sc # RECLAIMPOLICY pv回收策略,pod或pvc被删除后,pv是否删除还是保留。 # VOLUMEBINDINGMODE Immediate 模式下PVC与PV立即绑定,主要是不等待相关Pod调度完成,不关心其运行节点,直接完成绑定。相反的 WaitForFirstConsumer模式下需要等待Pod调度完成后进行PV绑定。 # ALLOWVOLUMEEXPANSION pvc扩容
1 2 3 4 5 6 7 8 9 10 11 # 2 下载并创建rbac # 因为storage自动创建pv需要经过kube-apiserver,所以需要授权
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 # 3 创建动态供给的deployment # 需要一个deployment来专门实现pv与pvc的自动创建 # 查看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 # 4 测试存储动态供给是否可用 # 应用 # 查看pv与pvc创建情况 # 查看pod
如果要删除stoarageclass/nfs-client
相关资源对象与配置,执行如下操作:
1 2 3 root@k8s03-1:/opt/kubeasz-deployk8s/deploy-kubesphere341/sc-nfs# kubectl delete -f deploy-nfs-client-provisioner.yml
2.2.6.3 手动创建sc/ceph
1 # 暂略,后续可能更新在个人github博客:https://jiangsanyin.github.io/archives/
2.2.6.4 下载kubesphere安装文件
1 2 3 root@k8s03-1:/opt/kubeasz-deployk8s/deploy-kubesphere341# wget https://github.com/kubesphere/ks-installer/releases/download/v3.4.1/kubesphere-installer.yaml
2.2.6.5 准备安装镜像
2.2.6.5.1 准备镜像清单文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 # 创建镜像清单文件 images-list-aliyuncs.txt # images-list-aliyuncs.txt文件内容如下 # 使用经验告诉笔者,如果只使用最基础的kubesphere功能,下列镜像列表可以进一步被裁剪(笔者暂未做裁剪) # # # # # # # # # #
1 2 # 下载offline-installation-tool.sh
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 # 如果不能正常下载,此处准备了此文件的内容,如下 # !/usr/bin/env bash # Copyright 2018 The KubeSphere Authors. # # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License.
使 .sh 文件可执行
1 chmod +x offline-installation-tool.sh
查看如何使用脚本
1 ./offline-installation-tool.sh -h
2.2.6.5.3 拉取镜像
1 root@k8s03-1:/opt/kubeasz-deployk8s/deploy-kubesphere341# ./offline-installation-tool.sh -s -l images-list-aliyuncs.txt -d ./kubesphere-images
2.2.6.6 推送镜像至私有仓库
1 2 3 4 5 # 推送到docker registry中 # 如果你已经按照前面的步骤安装了Harbor(默认已经创建一个library项目),此处还可以将镜像推送到Harbor仓库中 # root@k8s03-1:/opt/kubeasz-deployk8s/deploy-kubesphere341# ./offline-installation-tool.sh -l images-list-aliyuncs.txt -d ./kubesphere-images -r harbor.yourdomain.com:8444
2.2.6.7
修改ks-installer:v3.4.1镜像
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 # 不修改的话,的会提示“after connection broken by ‘SSLError(SSLCertVerificationError(1, ’[SSL: CERTIFICATE_VERIFY_FAILED] certifica”报错 # 创建Dockerfile文件,内容如下 # 修改kubesphere-installer.yaml 文件中使用的ks-installer镜像
2.2.6.8
上传镜像到指定registry项目下
1 2 # 创建push-image-to-easzlab.io.local.sh 文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 # push-image-to-easzlab.io.local.sh 文件内容如下 # !/bin/bash # 上传所有镜像到library项目下 # 使用 while 循环遍历每一行 # 经验证给部署kubesphere3.4.1过程中需要用到的镜像重新命名
1 2 # 执行push-image-to-easzlab.io.local.sh 文件
2.2.6.9 执行安装kubesphere
执行以下命令部署 KubeSphere:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 # 应用以下两个文件,以安装kubesphere # 查看安装进度与日志 # 给k8s集群的控制平台节点打标签 # 查看k8s集群的节点列表
使用vip+30880端口,可以正常访问kubesphere的web系统:
image-20241105111401577
2.2.6.10 从k8s中卸载kubesphere
1 2 3 4 # 参考:https://kubesphere.io/zh/docs/v3.4/installing-on-kubernetes/uninstall-kubesphere-from-k8s/
2.3 删除节点
参考:https://github.com/easzlab/kubeasz/blob/3.2.0/docs/op/op-node.md
删除 node 节点流程:(参考ezctl 里面del-node函数 和
playbooks/32.delnode.yml)
检测是否可以删除
迁移节点上的 pod
删除 node 相关服务及文件
从集群删除 node
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 # 删除节点前 # 删除节点(一次只能删除一个节点),它的IP是10.13.15.65 # 删除节点成功后
2.4 添加节点
新增kube_node节点大致流程为:(参考ezctl 里面add-node函数
和 playbooks/22.addnode.yml)
[可选]新节点安装 chrony 时间同步
新节点预处理 prepare
新节点安装 docker 服务
新节点安装 kube_node 服务
新节点安装网络插件相关
操作步骤 :
首先配置 ssh 免密码登录新增节点
1 2 3 4 5 # 一次只能添加一个节点(添加k8s节点前记得配置ssh免密登录) $ ezctl add-node k8s03 10.13.15.66 # 要添加多个节点,就执行添加节点命令多次 # 可能需要在新节点上执行:echo "10.13.15.61 easzlab.io.local" >> /etc/hosts
验证 :
1 2 3 4 5 6 7 # 验证新节点状态 $ kubectl get node # 验证新节点的网络插件calico 或flannel 的Pod 状态 $ kubectl get pod -n kube-system -o wide # 验证新建pod能否调度到新节点,略
2.5 卸载集群
在宿主机上,按照如下步骤清理
清理集群
docker exec -it kubeasz ezctl destroy <集群名称>
重启节点,以确保清理残留的虚拟网卡、路由等信息
操作步骤:
1 2 k8s03-1:/# ezctl destroy k8s03# 然后重启所有k8s节点
2.6 报错与处理
2.6.1
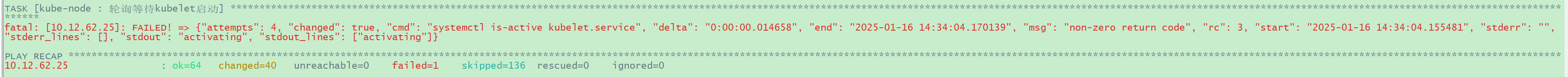
添加节点时“TASK [kube-node : 轮询等待kubelet启动]”执行失败
image-20250116143621421
问题定位:
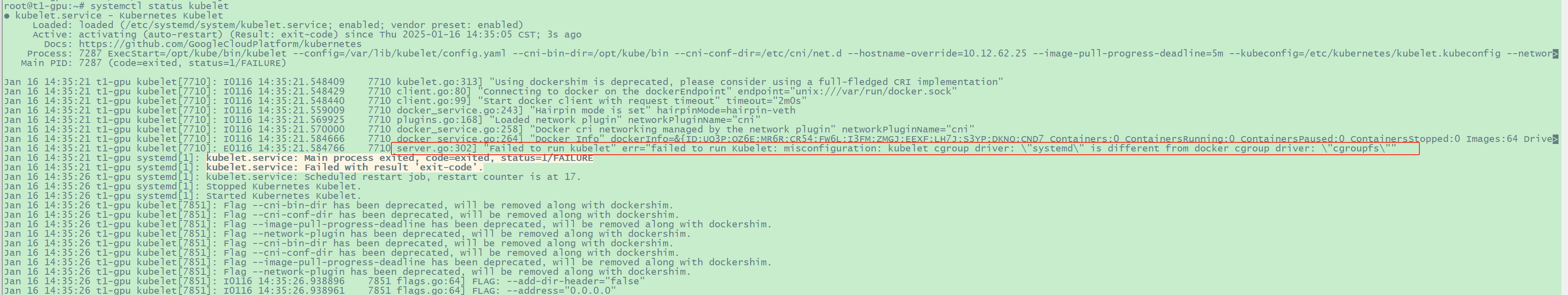
t1-gpu节点的ip是10.12.62.25,查看其上kubelet服务有如下报错信息:
image-20250116143749619
可知,使用kubeasz部署k8s时,安装的kubelet使用的 cgroup
driver是"systemd",但t1-gpu上现有docker cgroup driver
使用cgroupfs,修改t1-gpu上wget r docker cgroup driver
为systemd即可。
处理办法:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 # 在t1-gpu服务器的/etc/docker/daemon.json文件中添加如下内容 # 重启t1-gpu服务器的docker服务 # 然后在部署节点再次尝试添加k8s节点
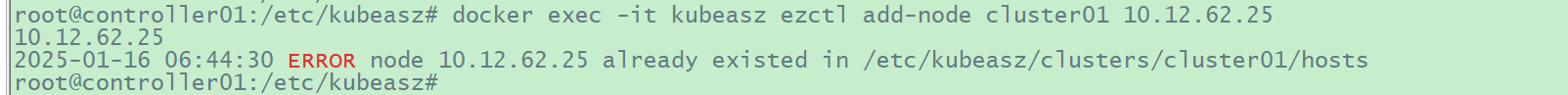
2.6.2
添加k8s节点时失败再次添加此节点时提示node已在hosts文件中
image-20250116144450943
处理办法:
1 2 3 4 5 6 7 8 9 10 # 在部署节点修改/etc/kubeasz/clusters/集群名/hosts # work node(s) # 192.168.1.3 # 192.168.1.4
然后在部署节点再次尝试添加k8s节点