2025年8月1日青云公告“自本公告发布之日起,将暂停 KubeSphere
开源版产品的下载链接,同时停止提供免费的技术支持”,相关详情见:https://ask.kubesphere.com.cn/forum/d/24963-guan-yu-kubespherekai-yuan-xiang-mu-diao-zheng-de-gong-gao
其官网开源文档已经删除,网上其他人整理的文档:https://kubesphere.saowu.top/zh/docs/v3.4/
一、环境信息介绍
主机名 IP root密码 规格 磁盘 操作系统 备注
ksp-deploy
172.25.253.106
cloud@123
4c8g
400g
Ubuntu 20.04.3 LTS-aarch64
联网,生成artifact等文件
node01
172.25.253.93
cloud@123
8c16g
400g
Ubuntu 20.04.3 LTS-aarch64
控制节点
node02
172.25.253.94
cloud@123
8c16g
400g
Ubuntu 20.04.3 LTS-aarch64
控制节点
node03
172.25.253.95
cloud@123
8c16g
400g
Ubuntu 20.04.3 LTS-aarch64
控制节点
node04
172.25.253.113
cloud@123
8c16g
400g
Ubuntu 20.04.3 LTS-aarch64
工作节点
node05
172.25.253.114
cloud@123
8c16g
400g
Ubuntu 20.04.3 LTS-aarch64
工作节点
环境涉及软件版本信息:
K8S节点操作系统:Ubuntu 20.04.3 LTS -aarch64
KubeSphere:v3.4.1
K8S:v1.23.17
Docker:24.0.6
KubeKey: v3.0.13
cni-plugins: v1.2.0
crictl: v1.24.0
etcd: v3.4.13
helm: v3.9.0
kubeadm、kubectl、kubelet: v1.23.17
KubeKey 使用
/var/lib/docker 作为默认路径来存储所有 Docker
相关文件(包括镜像)。建议添加附加存储卷(本文中未添加),分别给
/var/lib/docker 和 /mnt/registry 挂载至少
100G 。
本文假设联网的服务器ksp-deploy上相关基础操作如安装、配置docker等已经完成,未进行介绍说明。
二、离线安装介绍
KubeKey 从 v2.1.0 版开始新增了清单 (manifest) 和制品 (artifact)
的概念,为用户离线部署 KubeSphere 和 K8s
集群提供了一种简单便捷的解决方案。
manifest 是一个描述当前 Kubernetes 集群信息和定义 artifact
制品中需要包含哪些内容的文本文件。
使用 KubeKey,用户只需使用清单 manifest
文件来定义将要离线部署的集群环境需要的内容,再通过该 manifest 来导出制品
artifact 文件即可完成准备工作。离线部署时只需要 KubeKey 和 artifact
就可快速、简单的在环境中部署镜像仓库 Harbor 和 KubeSphere 以及 K8s
集群。
KubeKey 生成 manifest 文件有两种方式:
第一种方式的好处是可以根据 1:1
的运行集群构建离线集群,依赖于已有集群,灵活度不够,并不是所有人都具备这种条件。
但本文中涉及的是arm64构架服务器上搭建k8s1.23.17+ksp3.4.1环境,上述方法在amd64构架服务器上能成功,在此处不能成功(至少笔者自己未成功。其中笔者遇到失败之处就是不论是否使用harbor做镜像仓库,安装过程中都会尝试去下载harbor安装文件,但harbor官方并未提供arm64的安装文件,所以反复下载、反复失败)。所以笔者选择了逐步手动下载相关安装二进制文件、镜像与其他工具文件等,最后完成arm64构架服务器上k8s1.23.17+ksp3.4.1环境的安装部署。其中最关键的在于提前下载准备好离线安装k8s1.23.17+ksp3.4.1环境中用到Kubernetes二进制文件、Kubernetes与Kubesphere用到的镜像 ,其他的大致都是围绕此二者展开进行准备。
三、服务器的前置操作
建议所有服务器都要执行。
3.1 设置各服务器时区
1 timedatectl set-timezone Asia/Shanghai
3.2 设置各服务器主机名
1 2 hostnamectl set-hostname xxx# 然后退出终端并重新创建一个终端会话
3.3 设置主机与ip的映射信息
1 2 3 4 5 6 7 8 cat >> /etc/hosts <<EOF
3.4 设置时间同步
最好以离线k8s环境的某个节点做时间同步的源服务器。本文为了简化操作,未执行。生产环境中建议执行。
四、离线部署资源制作
制作离线部署资源需要找一台能联通互联网的节点(本文中是ksp-deploy),本文为了资源的制作和离线部署验证,单独增加了一个能联网的
ksp-deploy 节点。
在该节点下载 KubeKey (下文简称 KK)v3.0.13 。具体 KK
版本号可以在 KubeKey
发行页面 查看。
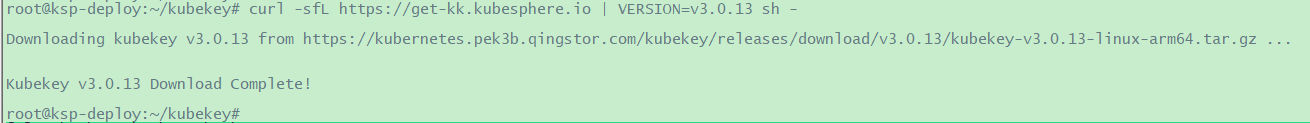
4.1 下载 KubeKey
1 2 3 4 5 6 root@ksp-deploy:~# mkdir /root/kubekey# 选择中文区下载(访问 GitHub 受限时使用) # 执行下载命令,获取指定版本的 kk(受限于网络可能会失败,可能需要执行多次)
image-20241228172413417
1 2 3 4 root@ksp-deploy:~/kubekey# chown root:root kk# 查看kubekey3.0.13版本
4.2 准备安装镜像
在 Linux 上安装 KubeSphere 和 Kubernetes
时,需要准备所有必需镜像文件,并事先下载 Kubernetes 二进制文件。
1 2 # 执行下面的命令获取官方 releases v3.4.1 对应的 images-list
但上述文件不能直接使用(从官网上下载下来的这个文件应该只是x86平台上验证过的。这个文件中有些镜像并没有对应arm64版本镜像;此外,非全量安装时不是所有镜像都是需要的)。
经过修改后image-list.txt文件如下(已经经过验证)。
1 root@ksp-deploy:~/kubekey# cat images-list.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 # # # # # # # # # #
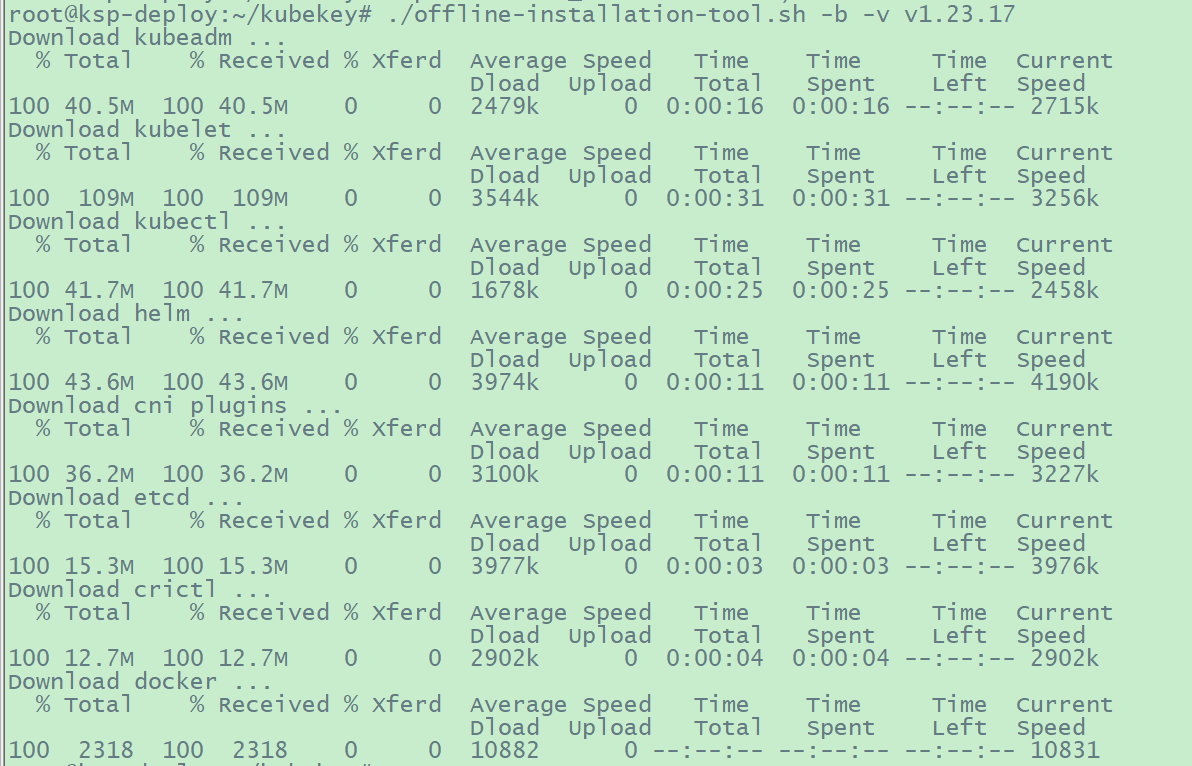
4.3 下载 Kubernetes 二进制文件
1 2 # 下载 offline-installation-tool.sh
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 root@ksp-deploy:~/kubekey# cat offline-installation-tool.sh# !/usr/bin/env bash # Copyright 2018 The KubeSphere Authors. # # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License.
1 2 3 4 5 6 7 8 9 10 # 给文件增加可执行权限 # 执查看如何使用脚本 # 下载 Kubernetes 二进制文件 # 运行脚本后,会在当前目录下自动创建一个文件夹 kubekey。请注意,后面创建集群时,该文件夹和 kk 必须放在同一个目录
image-20241230195525723
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 # 还需要下载一个calicoctl-linux-arm64 文件 # 查看创建的文件夹及下载的文件 # 笔者在下载时docker虽然显示成功但其实下载下来的 kubekey/v1.23.17/arm64/docker-24.0.6.tgz 文件只有2.3K,并不可用 # 于是手动重新下载
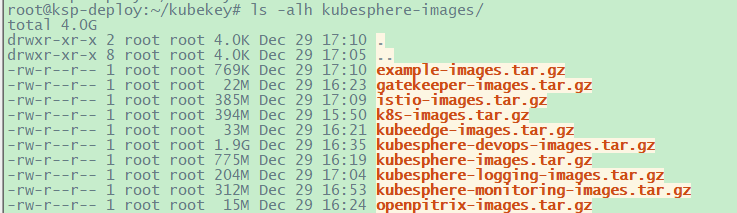
4.4 拉取部署过程中的镜像
1 2 root@ksp-deploy:~/kubekey# ./offline-installation-tool.sh -s -l images-list.txt -d ./kubesphere-images# 总共大概有4G左右
image-20241229171432036
4.5 准备registry:2镜像
1 2 root@ksp-deploy:~/kubekey# docker pull registry:2
4.6 打包压缩部署镜像文件
1 2 3 4 # 将 整个kubesphere-images/ 目录打包压缩成一个文件
4.7
准备与打包压缩依赖组件离线安装包
1 2 3 4 5 6 7 8 9 10 11 12 13 # 方法1:如下方法只下载部署k8s与kubesphere时需要用到的依赖组件 的离线安装文件 # 查看依赖: # 下载 deb 依赖包 # 打包压缩 # 方法2:真正在离线部署此类环境应该会准备一个操作系统的常用组件离线安装本地源,此处不展开阐述
4.8 打包压缩其他文件
1 2 3 4 # 把 KubeKey文件夹、kubekey-v3.0.13-linux-arm64.tar.gz、offline-installation-tool.sh等5个文件(夹)也制作成压缩包,便于拷贝到离线节点。
至此,我们已经准备了如下离线部署资源包:
部署镜像文件:kubesphere-images.tar.gz(4.0G)
部署工具文件:deploy-files.tar.gz(250M)
依赖组件离线安装包:dependent-components.tar.gz(6.8M)
五、部署 KSP 和 K8S
的前置准备操作
5.1
上传离线部署资源包到部署节点
将以下离线部署资源包(kubesphere-images.tar.gz、dependent-components.tar.gz与deploy-files.tar.gz
),上传至离线环境部署节点 (此处是 node01
节点,所有节点信息参考文档最开始处的描述) 的 /opt/deploy-k8s-ksp
目录(可根据实际情况修改)。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 # 创离线资源存放的数据目录 # 上传kubesphere-images.tar.gz与deploy-files.tar.gz 文件到node01:/opt/deploy-k8s-ksp 目录下 # 执行以下命令,解压相关文件: # 至此获得如下文件(夹)
1 2 3 4 5 6 7 8 # 可能能用上的代码段 # ssh-copy-id root@172.24.11.${ip}
5.2 安装docker容器服务
k8s集群的每个节点都要安装与配置。将node01节点上的
/opt/deploy-k8s-ksp/kubekey/v1.23.17/arm64/docker-24.0.6.tgz
复制到k8s集群的其他所有节点上,然后按照如下方式解压与部署docker服务。
1 2 3 4 # 按照如下方式解压与部署docker服务
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 # 使用systemd管理docker服务
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 # 配置docker守护进程配置文件:/etc/docker/daemon.json # 在 /etc/hosts 中添加一个条目,将主机名(即仓库域名;在本示例中是 dockerhub.kubekey.local)映射到docker resgistry所在服务器的私有 IP 地址,如下所示,以下规划172.25.253.93是docker resgistry所在服务器 # 应用上述文件并启动dicker服务,设置开机自启动 # 启动docker命令自动补全 # root@node01:/opt/deploy-k8s-ksp# echo "source <(docker completion bash)" >> /root/.bashrc # root@node01:/opt/deploy-k8s-ksp# source /root/.bashrc
5.3 安装依赖组件
k8s集群的每个节点都要安装与配置。将node01节点上的/opt/deploy-k8s-ksp/kubekey/dependent-components.tar.gz
复制到k8s集群的其他所有节点上,然后按照如下方式解压与安装依赖组件。
1 2 3 4 5 6 7 8 9 10 11 12 root@node01:/opt/deploy-k8s-ksp# tar -zxf dependent-components.tar.gz# 使用dpkg命令进行离线安装 # 可以先做好ssh免密登录 # 传输 dependent-components.tar.gz 到node01之外的其他k8s节点 /opt/deploy-k8s-ksp/ 目录下 # k8s集群所有节点安装依赖组件
5.4 准备一个私有镜像仓库
Harbor官方未提供harbor安装文件,虽然笔者已经找到在arm64服务器上部署harbor的方法,但本文以
Docker 仓库作为镜像仓库存储k8s部署过程中需要用到的镜像,并使用自签名证书 。
本文在node01上搭建 Docker 仓库。
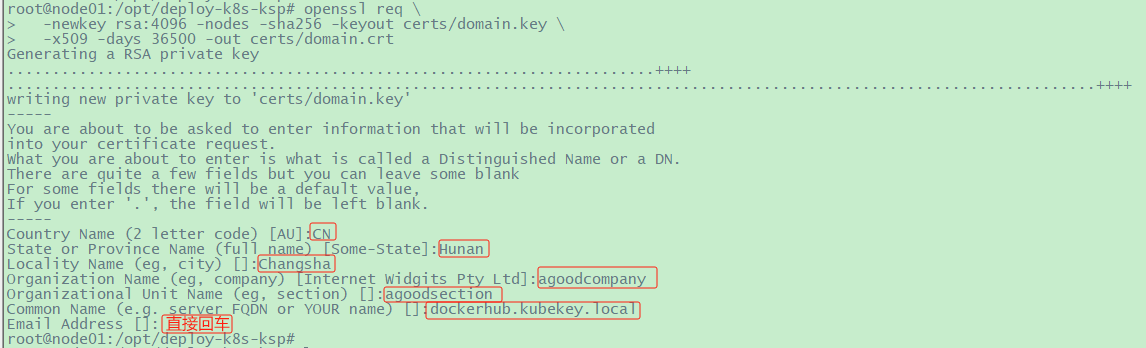
使用自签名证书
1 2 3 4 5 # 执行以下命令生成您自己的证书
image-20241229221911321
启动 Docker 仓库
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 # 加载registry:2镜像 # 让Docker信任刚生成的证书(所有节点都需要此证书。但registry容器只存在于部署节点上,此处部署节点是node01) # 执行以下命令启动 Docker 仓库
验证仓库
1 2 3 4 # 要验证私有仓库是否有效,可以修改镜像registry:2的namespace,然后使用 docker push 和 docker pull 来测试。
5.5 推送镜像至私有仓库
1 2 3 # 将打包的镜像文件传输至您的本地机器,并运行以下命令把它推送至仓库 # 命令中的域名是 dockerhub.kubekey.local,它是docker registry仓库的别名
5.6 创建离线集群配置文件
1 2 3 4 5 # 执行以下命令创建离线集群配置文件 # 如果在这一步的命令中不添加标志 --with-kubesphere,则不会部署 KubeSphere,只能使用配置文件中的 addons 字段安装,或者后续使用 ./kk create cluster 命令时再次添加这个标志。
命令执行成功后,在当前目录会生成文件名为 ksp-v341-v12317-offline.yaml
的配置文件。
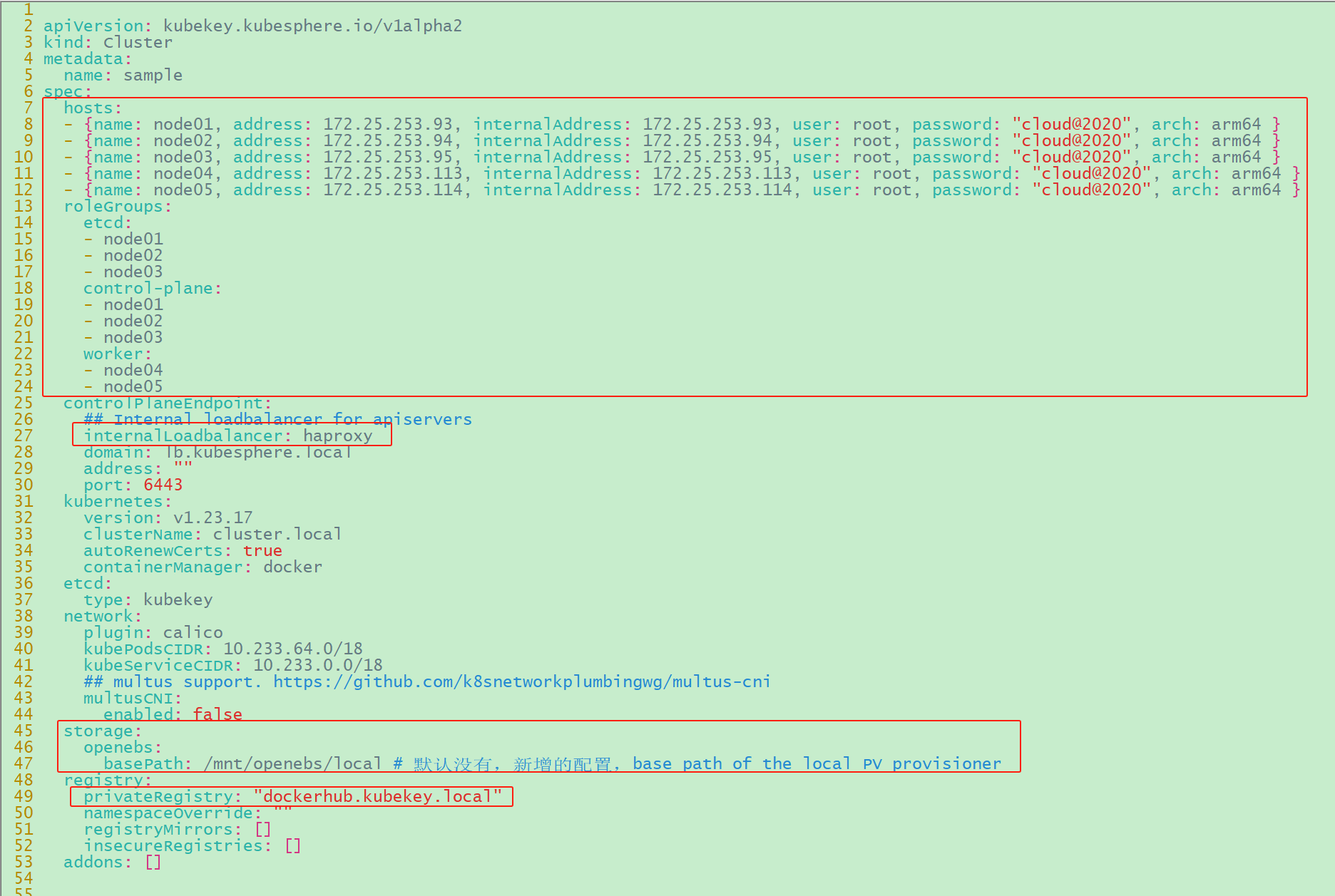
5.7 修改 Cluster 配置
在离线集群配置文件文件中 kind: Cluster
小节的作用是部署 Kubernetes 集群。本文示例采用 3 个节点同时作为
control-plane、etcd 节点,两个节点作为 worker 节点。
1 2 # 执行以下命令修改离线集群配置文件 ksp-v341-v12317-offline.yaml
修改 kind: Cluster 小节中 hosts 和 roleGroups
等信息,修改说明如下。
hosts:指定节点的
IP、ssh登录用户、ssh登录密码,并指明服务器构架。
roleGroups:指定 3 个 etcd、control-plane 节点,2 个 worker
节点
修改controlPlaneEndpoint组的配置:
internalLoadbalancer: 启用内置的 HAProxy 负载均衡器
添加storage组的配置:
storage.openebs.basePath:新增配置 ,指定 openebs
默认存储路径为 /data/openebs/local
修改registry组的配置:
registry:使用 docker
registry,它的地址是"dockerhub.kubekey.local"
修改或添加的内容如下(其余保持默认):
image-20241230203614561
5.8 最后的配置
经过上述步骤,我们成功完成了对离线集群配置文件
ksp-v341-v12317-offline.yaml 的修改。此时,修改后的
ksp-v341-v12317-offline.yaml文件如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 apiVersion: kubekey.kubesphere.io/v1alpha2 kind: Cluster metadata: name: sample spec: hosts: - {name: node01 , address: 172.25 .253 .93 , internalAddress: 172.25 .253 .93 , user: root , password: "cloud@123" , arch: arm64 }- {name: node02 , address: 172.25 .253 .94 , internalAddress: 172.25 .253 .94 , user: root , password: "cloud@123" , arch: arm64 }- {name: node03 , address: 172.25 .253 .95 , internalAddress: 172.25 .253 .95 , user: root , password: "cloud@123" , arch: arm64 }- {name: node04 , address: 172.25 .253 .113 , internalAddress: 172.25 .253 .113 , user: root , password: "cloud@123" , arch: arm64 }- {name: node05 , address: 172.25 .253 .114 , internalAddress: 172.25 .253 .114 , user: root , password: "cloud@123" , arch: arm64 }roleGroups: etcd: - node01 - node02 - node03 control-plane: - node01 - node02 - node03 worker: - node04 - node05 controlPlaneEndpoint: internalLoadbalancer: haproxy domain: lb.kubesphere.local address: "" port: 6443 kubernetes: version: v1.23.17 clusterName: cluster.local autoRenewCerts: true containerManager: docker etcd: type: kubekey network: plugin: calico kubePodsCIDR: 10.233 .64 .0 /18 kubeServiceCIDR: 10.233 .0 .0 /18 multusCNI: enabled: false storage: openebs: basePath: /mnt/openebs/local registry: privateRegistry: "dockerhub.kubekey.local" namespaceOverride: "" registryMirrors: []insecureRegistries: []addons: []--- apiVersion: installer.kubesphere.io/v1alpha1 kind: ClusterConfiguration metadata: name: ks-installer namespace: kubesphere-system labels: version: v3.4.1 spec: persistence: storageClass: "" authentication: jwtSecret: "" local_registry: "" etcd: monitoring: false endpointIps: localhost port: 2379 tlsEnable: true common: core: console: enableMultiLogin: true port: 30880 type: NodePort redis: enabled: false enableHA: false volumeSize: 2Gi openldap: enabled: false volumeSize: 2Gi minio: volumeSize: 20Gi monitoring: endpoint: http://prometheus-operated.kubesphere-monitoring-system.svc:9090 GPUMonitoring: enabled: false gpu: kinds: - resourceName: "nvidia.com/gpu" resourceType: "GPU" default: true es: enabled: false logMaxAge: 7 elkPrefix: logstash basicAuth: enabled: false username: "" password: "" externalElasticsearchHost: "" externalElasticsearchPort: "" opensearch: enabled: true logMaxAge: 7 opensearchPrefix: whizard basicAuth: enabled: true username: "admin" password: "admin" externalOpensearchHost: "" externalOpensearchPort: "" dashboard: enabled: false alerting: enabled: false auditing: enabled: false devops: enabled: false jenkinsCpuReq: 0.5 jenkinsCpuLim: 1 jenkinsMemoryReq: 4Gi jenkinsMemoryLim: 4Gi jenkinsVolumeSize: 16Gi events: enabled: false ruler: enabled: true replicas: 2 logging: enabled: false logsidecar: enabled: true replicas: 2 metrics_server: enabled: false monitoring: storageClass: "" node_exporter: port: 9100 gpu: nvidia_dcgm_exporter: enabled: false multicluster: clusterRole: none network: networkpolicy: enabled: false ippool: type: none topology: type: none openpitrix: store: enabled: false servicemesh: enabled: false istio: components: ingressGateways: - name: istio-ingressgateway enabled: false cni: enabled: false edgeruntime: enabled: false kubeedge: enabled: false cloudCore: cloudHub: advertiseAddress: - "" service: cloudhubNodePort: "30000" cloudhubQuicNodePort: "30001" cloudhubHttpsNodePort: "30002" cloudstreamNodePort: "30003" tunnelNodePort: "30004" iptables-manager: enabled: true mode: "external" gatekeeper: enabled: false terminal: timeout: 600
5.9 安装配置 Harbor
arm64服务器上搭建harbor环境可以参考:https://jiangsanyin.github.io/2024/10/30/arm64%E6%9C%8D%E5%8A%A1%E5%99%A8%E4%B8%8B%E7%9A%84Harbor-v2-11-1%E7%8E%AF%E5%A2%83%E6%90%AD%E5%BB%BA/。
后续用法跟x86_64构架服务器上的harbor一样。
六、安装 KubeSphere 和 K8s
集群
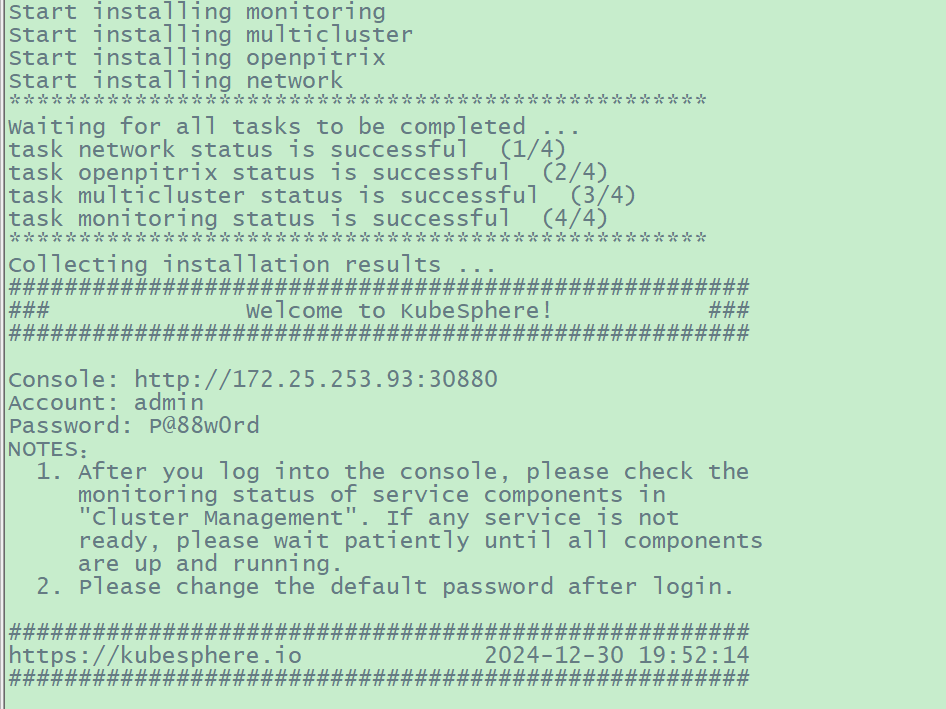
6.1 执行安装KubeSphere 和 K8s
集群
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 # 创建mkdir-copyfile.sh # 其内容如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 # 如果 /mnt/openebs/local 目录非空,请将此目录下的所有文件清空,否则安装将失败、提示如下 # TASK [common : debug] ********************************************************** # ok: [localhost] => { # "msg" : [ # "1. check the storage configuration and storage server" , # "2. make sure the DNS address in /etc/resolv.conf is available" , # "3. execute 'kubectl logs -n kubesphere-system -l job-name=minio-make-bucket-job' to watch logs" , # "4. execute 'helm -n kubesphere-system uninstall ks-minio && kubectl -n kubesphere-system delete job minio-make-bucket-job'" , # "5. Restart the installer pod in kubesphere-system namespace" # ] # } # 执行以下命令,安装 KubeSphere 和 K8s 集群
参数说明:
ksp-v341-v12317-offline.yaml :离线环境集群的配置文件
上面的命令执行后,首先 KubeKey 会检查部署 K8s
的依赖及其他详细要求。检查合格后,系统将提示确认安装。输入
yes 并按 ENTER 继续部署。
image-20241230205705028
6.2 部署后置处理
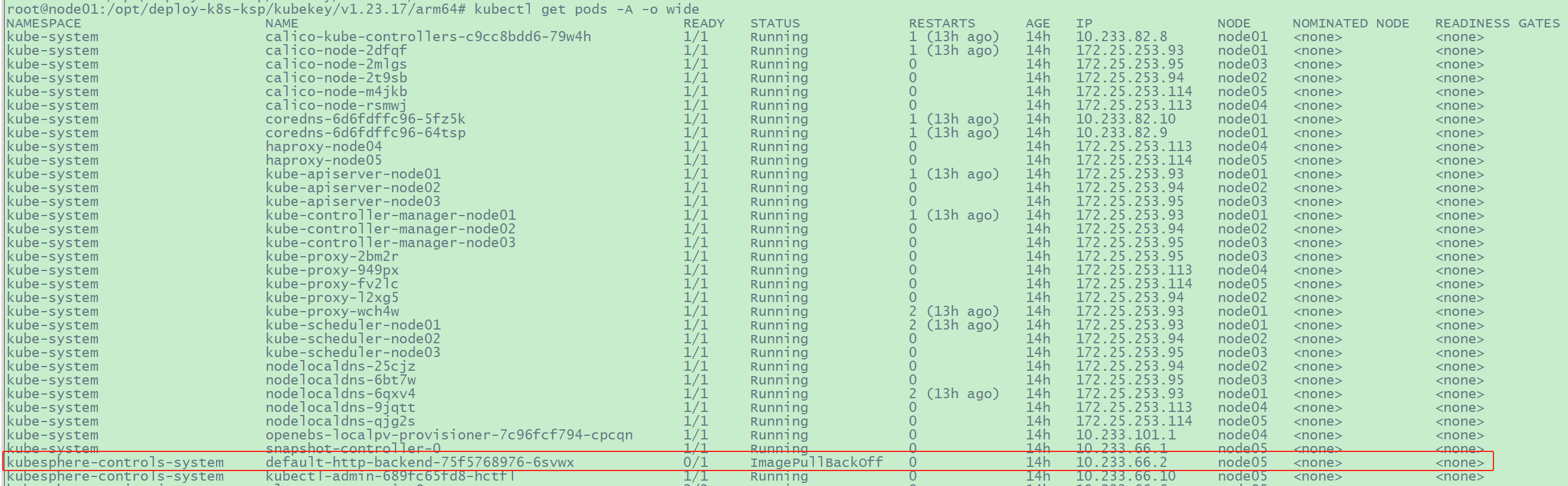
6.2.1
pod/default-http-backend-75f5768976-6svwx 一直处于ImagePullBackOff
状态
image-20241231095318516
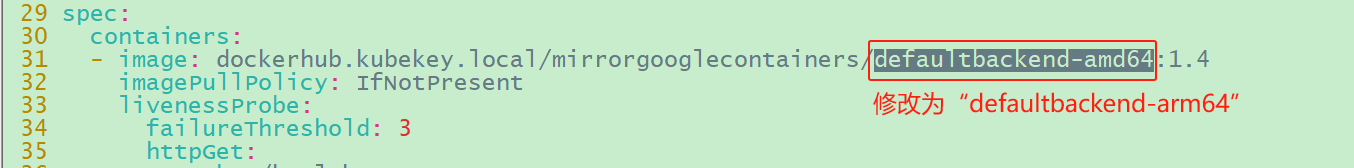
因为安装程序尝试拉取与使用的镜像是amd64构架镜像,应该是安装程序(具体地说是kk工具)内部的错误。且在此处私有镜像镜像仓库中尝试拉取的镜像并不存在,所以一直拉取不成功。
1 2 3 # 修改 命名空间kubesphere-controls-system下的pod/default-http-backend-75f5768976-6svwx # 将spec中使用的镜像修改为“dockerhub.kubekey.local/mirrorgooglecontainers/defaultbackend-arm64:1.4”
image-20241231095456573
image-20250808113150044
1 2 3 4 5 6 # 在各节点执行如下命令即可,原因暂不清楚
6.3 控制节点配置keepalived
暂略。配置keepalived相关方法可以参考:https://jiangsanyin.github.io/2024/08/10/%E6%90%AD%E5%BB%BA%E4%BA%92%E4%B8%BA%E4%B8%BB%E5%A4%87MySQL5-7%E9%9B%86%E7%BE%A4%E5%B9%B6%E5%AE%9E%E7%8E%B0%E8%87%AA%E5%8A%A8%E5%88%87%E6%8D%A2/#2-3-%E5%AE%89%E8%A3%85%E4%B8%8E%E9%85%8D%E7%BD%AEkeepalived
七、部署结果验证
访问kubesphere3.4.1的web管理界面: http://172.25.253.93:30880/login
。默认用户名:admin,其默认密码:P@88w0rd
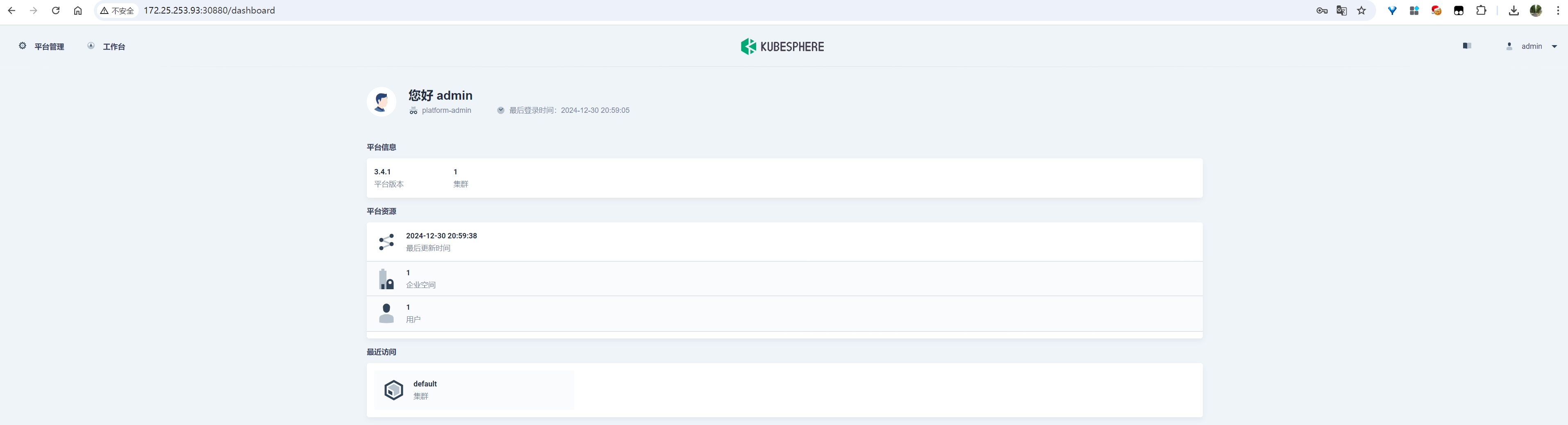
登录成功后看到的界面:
image-20241230205947409
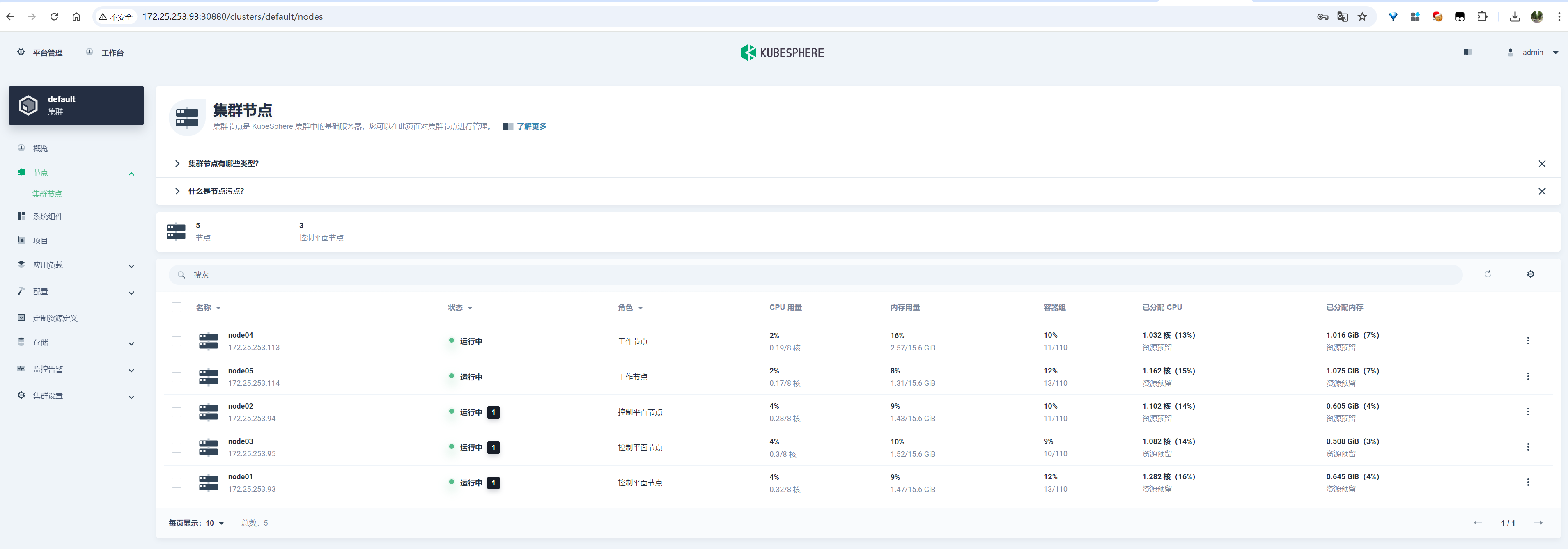
查看节点状态:
image-20241230205929259
八、参考文档
https://v3-1.docs.kubesphere.io/zh/docs/installing-on-linux/introduction/air-gapped-installation/